This article is half-done without your Comment! *** Please share your thoughts via Comment ***
Prior to Cassandra 2.2, it supports only User base authentication, but now Cassandra introduces new Role-based authentication.
In this post, I am sharing a demonstration on how to create a Role in Cassandra and How to assign different permissions to that role.
You can directly use this Role for authentication and you can also assign same Role permission to another role.
First, login with Cassandra’s super user.
|
1 |
cqlsh -u cassanddra -p cassandra |
Create keyspace if not exists:
|
1 2 3 |
CREATE KEYSPACE IF NOT EXISTS dbrnd WITH replication = {'class': 'SimpleStrategy', 'replication_factor' : 3}; USE dbrnd; |
Create few sample tables:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 |
CREATE TABLE IF NOT EXISTS tbl_Employee ( EmpID INT PRIMARY KEY ,EmpFirstName VARCHAR ,EmpLastName VARCHAR ,EmpSalary INT ); CREATE TABLE IF NOT EXISTS tbl_Department ( DeptID INT PRIMARY KEY ,DeptName VARCHAR ); |
Create one sample Role without Superuser access:
If you get this error : “org.apache.cassandra.auth.CassandraRoleManager doesn’t support PASSWORD”, visit this solution.
|
1 |
CREATE ROLE ReportingRole WITH PASSWORD = 'pass123' AND LOGIN = true AND SUPERUSER = false; |
Grant different permissions to this Role:
|
1 2 |
GRANT SELECT ON dbrnd.tbl_Employee TO ReportingRole; GRANT MODIFY ON dbrnd.tbl_Department TO ReportingRole; |
If you get any error like ” GRANT operation is not supported by AllowAllAuthorizer”, you have to modify the value of “authorizer” in cassandra.yaml file.
|
1 2 3 4 5 |
-- Old value: authorizer: AllowAllAuthorizer -- Change to this New value: authorizer: org.apache.cassandra.auth.CassandraAuthorizer |
Grant over the all keyspaces:
|
1 2 |
GRANT SELECT ON ALL KEYSPACES TO ReportingRole; GRANT MODIFY ON ALL KEYSPACES TO ReportingRole; |
Create new test Role and make it a replica of the current role:
|
1 2 3 |
CREATE ROLE Test WITH PASSWORD = 'pass123' AND LOGIN = true AND SUPERUSER = false; GRANT ReportingRole to Test; |
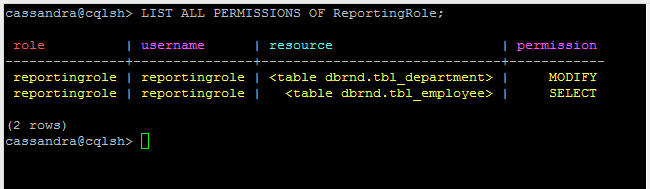
List out all Roles and its permissions:
|
1 2 3 4 |
-- List out all Roles. LIST ROLES; -- List out all permissions of the Role. LIST ALL PERMISSIONS OF ReportingRole; |